Native Vs Cross-platform App Growth: What To Choose In 2024 By Rashad Shirizada Codex
This bridging method preserves near-native speed and look by tapping into platform-specific parts while letting developers maintain the bulk of their logic in JavaScript. In Flutter vs React Native comparisons, this reliance on bridging stands out as React Native’s defining feature, significantly for teams trying to take advantage of https://boxoxmoving.com/blog/category/austin-residential-packing/page/3/index.html present JavaScript experience. Assess the extent of flexibility and customization required on your project. Some frameworks, like Xamarin, may supply extra management over the native parts, while others prioritize ease of use and speedy growth. If your group is proficient in a specific language or framework, it might affect your alternative. For example, in case your group has expertise in JavaScript, frameworks like React Native or Ionic might be more suitable.
Security Of The Applying
Hence, native apps are designed completely for a selected mobile platform. Developing an app with a particular platform (IOS or Android apps) permits developers to leverage all the possible choices absolutely it supplies without needing to make compromises for other kinds of gadgets. Choosing between native app improvement vs. cross-platform is difficult, as both approaches have advantages and risks.
Cross-platform Vs Native App – What To Choose On In Your Project?
Native cell functions are those made specifically for iOS or Android platforms. Generally, the programming language you select to create your apps often varies relying on the operating system that they are meant for. Several highly effective instruments dominate the landscape in relation to constructing cross-platform apps. Facebook’s React Native allows builders to discover their JavaScript proficiency to create user-friendly and environment friendly applications for each Android and iOS. Google’s Flutter, utilizing the Dart programming language, presents a fast improvement cycle and visually interesting interfaces. Cross-platform apps run on a digital machine or via an additional abstraction layer, leading to slower efficiency than native apps.
If you rent top cross-platform builders, they may handle to build your cross-platform app in a method that provides customers with nearly the same experience. Depending on the functionality, you can nonetheless encounter issues, and the app could be a bit slower than the native one, however typically, there won’t be any noticeable difference. That becomes burdensome to hold up should you improve the amount of custom native modules an extreme amount of, especially when they’re very complex. When the custom native a half of the app is larger than the cross-platform one, it’s time for redevelopment.
In many instances, the situation leads to the dearth of attention to one of many versions or the absence of sources concerning development. Since developing apps for Android and iOS are separate, this means they will also have a separate codebase. Developers have to be prepared to implement each new app function twice for the rationale that platforms are totally different.
By utilizing a shared codebase, Airbnb was in a position to streamline its growth process and guarantee consistent functionality across platforms. This strategy allowed the company to focus on delivering a superior consumer expertise while decreasing development time and prices. As the examples show, cross-platform improvement is very well-liked on desktop platforms. What’s the reason to consider cross-platform apps vs. native apps there? PC operating techniques have many distinctive platform-specific apps (for occasion, macOS is understood for its unique video and audio enhancing software). Platforms such as Electron reduce the necessity to change between platforms for varied objectives.
Crafting cross-platform mobile functions takes much less time than native development (about ⅔ of it) on one condition — if your resolution has no native-related capabilities, which is never the case. When native plugins enter the scene, cross-platform growth experiences setbacks and spikes in price. Cross-platform apps are built using frameworks that permit builders to write a single codebase that runs on a number of platforms, similar to iOS and Android. Popular frameworks like Flutter, React Native, and Xamarin have made cross-platform growth increasingly engaging. React Native is an open-source JavaScript improvement framework that makes use of ReactJS to create person interfaces for iOS and Android units. The framework additionally allows you to write modules in different languages similar to Swift, Python and C++.
The cross-platform vs. native apps contest has a transparent winner regarding customization too. Due to having higher integration with platform-specific APIs, this approach permits accessing deeper operating system features. Cross-platform frameworks could not present full entry to all native APIs and functionalities, potentially restricting the app’s capabilities or requiring custom plugins to bridge the hole. Integrating Siri on iOS is rather more tough with cross-platform quite than native apps. Updating and maintaining a single codebase simplifies the method, as modifications may be utilized universally, saving time and resources. Releasing updates (both security- and feature-centric ones) is simple with cross-platform apps.
Read this post to seek out out an important developments that may form the future of the internet. We’ll be joyful to work on your project — inform us about your future app in the contact type beneath. SDKs may additionally be streamlined with pieces of code and libraries which are frequently updated and (usually) prepared for implementation, full with technical guides and documentation. Apps made for the native environment are additionally extra scalable because of the freedom in useful resource administration and the variety of instruments obtainable. Enhancing accessibility in Customer Relationship Management (CRM) opens doors for inclusivity.
- Cross-platform growth goals to achieve a stability between efficiency and agility, whereas hybrid development trades off some performance.
- Some in style cross platform frameworks include React Native, Flutter, and Xamarin.
- Finally, you will learn the best practices of consumer interface design and get an understanding of building a responsive and adaptive UI using Flutter.
- By preserving up-to-date with new options and enhancements, developers can continually improve their applications and ship superior user experiences.
- However, I don’t recommend you constructing more than a few features this way (but you probably can nonetheless build even a core feature of your MVP app) as the app turns into overcomplicated.
It’s your greatest option if you don’t wish to spend too much cash but wish to offer your app to Android and iOS customers at once. It’s not obvious, but you could also construct a cross-platform app for one platform only (iOS, for example). In the rapidly evolving world of cellular app improvement, the controversy between cross-platform and native apps stays a important decision for businesses in 2025. Choosing the best development approach can significantly impact your app’s efficiency, cost, and consumer satisfaction. Let’s explore the professionals and cons of each choice that can help you make an knowledgeable determination.
Sometimes, nonetheless, you may not need to use a browser but present customers with a downloadable app. If it’s a easy mobile utility and you continue to want an internet app at the identical time, a Progressive Web App would be the greatest match. Therefore, Responsive Web Apps are completely different from different apps talked about on this article because they aren’t put in on cellular devices. In fact, this isn’t one of many typical mobile apps but an online app that looks good on cell gadgets (and is based on a Responsive Web Design). You don’t have a year to spend on growth — in this case, cross-platform frameworks are a greater choice.
The cross-platform approach revolves around the idea of platform-agnostic functions and a single codebase for various platforms. Native application development means constructing a cellular utility for a specific platform (iOS or Android) by utilizing tools which are “native” to this platform (in other words, intended to be used on it). In this fashion, a local app written for the iOS platform will not run on Android and vice versa. Developers can reuse a good portion of code throughout platforms, decreasing development effort and time. Obviously, cross-app improvement still requires some unique platform-specific code.
Testing On Selenium Cloud : The Greatest Way Forward
This means you probably can run your exams on totally different browsers and operating techniques using the Command-line Runner. In data-driven testing, Selenium is integrated with data dealing with tools to check websites crm development under various information situations. It processes multiple units of enter data, validating the website’s conduct in each scenario.
Selecting A Software Program Testing Provider

You can run tests on a selection of selenium cloud browsers and units, and you don’t have to fret about managing complex on-premises setups. Cloud-based testing can be reliable and fast, so that you can be assured that your software program is high-quality. Selenium WebDriver is a component of the Selenium suite for automating web application testing. It offers an interface for builders and testers to create and run take a look at scripts, which simulate consumer interactions with web browsers. This contains actions like clicking on links, filling out forms, and fetching internet page data.
Software Program Testing Providers: An Entire Guide
Selenium enables automated test execution throughout varied programming languages. Depending on the language chosen for the test script, similar to Java or JavaScript, there are some conditions, setup, and execution processes you should follow. Selecting a check automation framework is an important choice in the automation testing process. The right framework should match the staff’s expertise and be evaluated based on ease of use, scalability, and ability to handle advanced test cases. In Selenium three, communication relied on the JSON Wire Protocol over HTTP, where language bindings (like C#, Java, Ruby, and Python) communicated immediately with the browser driver. The protocol acted as a bridge, as the server only understood these protocols, not the programming languages.
Exception Dealing With In Selenium Webdriver
Test your web site performance and UI on varied cell gadgets and variations, with geolocation help. Drastically shorten your total Selenium test period by running checks concurrently. TestingBot provides single-use VMs on Windows, Linux and macOS, optimized for speed and stability. Test Geo Targeting, Geo Blocking and Geo Localization in 10 nations, together with Australia, Belgium, United Kingdom, United States, Germany, France, Spain, China and extra. Each Selenium test result comes with screenshots, logs and a video of the test. Mark Selenium exams as passed or failed, retrieve check artifacts via our REST-API and join your check outcomes through various integrations.
Shift-left testing emphasizes early testing within the software improvement lifecycle. Instead of ready until the end, this strategy includes steady testing throughout—from design and development to deployment. Catching defects early reduces the cost and time of fixing them, leading to quicker delivery and higher high quality. Shift-left testing additionally improves collaboration between builders and testers, creating shared responsibility for quality.
AI and ML are key to enabling shift-left testing by way of automated test execution and continuous feedback. This proactive strategy is more and more essential as organizations prioritize delivering high-quality software shortly. Clearly outlined testing necessities are the inspiration of a profitable testing technique. Before you start testing, take the time to totally understand the software’s functionality, target audience, and performance expectations. This includes outlining specific check circumstances, defining acceptance criteria, and figuring out potential dangers.

This grid is right for implementing automated tests throughout browsers and gadgets. Agile and DevOps methodologies encourage continuous testing throughout the event lifecycle. Instead of large, rare releases, improvement groups deliver smaller, functional updates extra incessantly. This permits for more focused and comprehensive testing at each step, catching bugs early and reducing the price of fixing them later. Testers work intently with builders, guaranteeing that testing just isn’t an afterthought however a core element of the event course of.
This strong documentation ensures transparency and accountability all through the testing process, facilitating better communication and collaboration amongst group members. It could be built-in with varied testing frameworks provided by Selenium-supported languages, such as TestNG, JUnit, TestCafe, and others. This integration streamlines the automation testing course of by leveraging totally different capabilities of a framework. Selenium, a strong open-source software, has gained immense recognition in the subject of automated testing as a outcome of its flexibility and versatility.
In Selenium testing, it’s beneficial to avoid using blocking sleep calls like Thread.sleep or time.sleep. These calls stop the take a look at thread, probably delaying the take a look at execution and not all the time guaranteeing effective timing as a result of exterior elements like community pace and server load. While there aren’t strict pointers for creating scalable automation tests, sure key rules must be adhered to when creating checks with the Selenium framework.
Selenium is an open-source software that’s used for automating the checks carried out on net browsers. Multiple programming languages like Java, C#, and Python are used to create Selenium Test Scripts. Testing done using the Selenium testing software is usually referred to as Selenium Automation Testing.
Automated UI testing with Selenium tests the UI parts like buttons, textual content fields, and menus, ensuring they don’t appear to be solely current and visual but also functional and responsive. This testing verifies the usability and aesthetic features of the website. With Selenium, you’ll have the ability to simulate actual consumer interactions by replicating mouse behaviors and keyboard events. This enables automated testing after code changes, which will assist find defects early. The Page Object Model is a design sample by which you create a class for every internet page and, inside each class, define the component of that web page.
For software program testers, this translates to extra diversified testing and tighter deadlines. When the complete business world is leaning on the idea of digital transformation by working on software and purposes.. In addition to our expertise with Selenium Testing Services, the Apexon staff has also done intensive, hands-on work with other main take a look at automation instruments. We might help you are taking full benefit of those capabilities together with Selenium, or individually, based mostly on your wants. With Scalo Selenium-based software program testing, your internet project has an excellent probability of rapidly showing on the market and shining with the glow of reliability. Parallel testing in Selenium involves operating a check automation suite or take a look at cases in parallel.
Do you wish to improve the efficiency of your software program improvement course of and deliver higher… Software initiatives usually evolve, and altering necessities can disrupt testing plans. Last-minute adjustments can be difficult, but flexibility is crucial. Prioritize testing efforts primarily based on the revised requirements, specializing in high-risk areas. Embrace agile methodologies that accommodate change and think about using take a look at automation to shortly adapt.
- From a developer’s vantage point, the primary target is on enhancing the feature set, dashing up the general efficiency, and constructing a scalable product.
- MuukTest combines an AI-powered platform with seasoned QA professionals to deliver comprehensive software program testing providers.
- This protocol allows for direct communication between the server and the consumer, eliminating the need for the JSON Wire Protocol.
- DevOps engineers use Selenium to automate the testing course of as part of the CI/CD pipeline.
This strategy not only enhances test coverage but also ensures the robustness of the net site across different data-driven use circumstances. In functional testing, Selenium is used to validate if the website features according to the required requirements. It automates the execution of tests that check specific functionalities, simulating person interactions like clicking, typing, and navigation. Parallel testing with Selenium includes executing multiple test suites or check circumstances concurrently to scale back the general testing time. You can carry out parallel testing either domestically or on a cloud-based grid, effectively reducing your software program launch cycles. Developers also use Selenium to implement and validate the functionality of internet options in the course of the growth part.
This service offers a few of the finest features to cut back your prices in addition to testing efforts. This browser matrix comes from analyzing product knowledge, geolocation, and detailed insights about how your audience uses completely different browsers. It also involves looking at statistics, such because the number of users on each browser, and analyzing your competitors.
Transform Your Business With AI Software Development Solutions https://www.globalcloudteam.com/ — be successful, be the first!
Software Testing Implementation Testing
Some of the processes on this approach include ensuring alignment between trade requirements and testing actions and meeting set quality criteria. Testers normally implementation testing conduct testing in a controlled and structured manner which ensures the auditability, reproducibility, and traceability of assorted actions. This method enables consistent and environment friendly testing compliant with established norms.
Step 5 Launch Control: Managing The Launch
Also, at the operational level, storing a test plan in a GitHub repo makes it simple to provide the evaluate, acceptance and audit path needed for structured change management Application Migration. A test plan needs to describe the data that will be gathered and evaluated for reporting. In terms of test data, there’s operational check reporting and project degree check reporting. As such, the check plan wants to explain the logging or database expertise used, the place the data will reside and how the information might be accessed. Many testing frameworks will retailer only the outcomes of the final test suite run.
Significance Of Test Closure Activities In Testing Process
Stay updated with LambdaTest YouTube Channel to get in-depth tutorials on Selenium automation, Cypress testing, Playwright testing, and more. Apart from considering these factors whereas selecting the sort of strategy, testers must additionally contemplate some other features earlier than crafting the ideal strategy. It is crucial to choose on the best kind and arrange the information actually without underestimating the benefits this document brings. Learn what agile software program requirement specs (SRS) are their importance, and their part…
Take A Look At Execution In Software Program Testing
Also, within the case in which input has no direct output, a black field check will assess some aspect of the system overall. This would be the first introduction to the model new system for many finish customers and is essentially the most complex time logistically. Developing a take a look at strategy and check plan for your software or system is a crucial step in the means of implementation. UAT entails end-users testing the software program to ensure it meets their needs and necessities. It aims to achieve consumer suggestions and validate whether the software aligns with user expectations earlier than its final release. Performance testing evaluates the software’s responsiveness, speed, scalability, and stability beneath different circumstances.
They use this partial knowledge to design check cases that target particular areas or functionalities of the software program. The primary objective is to validate that the software capabilities accurately and aligns with the expected conduct with out considering its inner mechanics. Testers give consideration to inputs, outputs, and interactions with the software program to determine defects corresponding to incorrect outputs, missing features, or usability issues. Independent testers or QA groups typically perform black box testing and do not require programming data.
The integration of steady integration (CI) practices helps detect and resolve integration points early. Ensure these check cases are detailed and include each practical and non-functional necessities. The subsequent step is to design take a look at circumstances that address all attainable interactions between application layers. This approach tests particular person elements and their interactions, resulting in a extra reliable and robust software.
Some tests plans will depend upon the storage features of test framework to be certain that test data is saved and retrievable. Other times, saving take a look at results might need to happen by way of logs or in a database. Explore the highly effective capabilities of Oracle Financial Close and Consolidation Supplemental Data Manager (SDM). Learn how SDM simplifies managing supplemental data, enhances advert hoc information collection, helps detailed disclosures, and streamlines business processes. ” To determine if the test was successful, monitor the resulting every day metrics of the take a look at, just like the variety of exams executed and number of checks completed and didn’t create a burndown report. Using these metrics can confirm whether you’re on monitor in the direction of profitable implementation.
The section contains the fixed comparability of the present progress of a project towards the metrics defined within the take a look at plan. Test management entails taking actions wanted to meet the plan’s goals, which may undergo particular adjustments over time. It is referred to as the definition of carried out in some software improvement lifecycle models. Software Testing Life Cycle (STLC) is a sequence of different activities carried out by a testing staff.
Responsibilities of this position include reviewing all testing reports and dashboards and all concern resolution actions. The operational steering committee also coordinates communication of testing efforts to the chief steering committee and ensures last sign-off on User Acceptance Testing outcomes. The project plan must be evaluated throughout all phases of the project.
While sandwich integration testing provides many advantages, it additionally comes with its personal set of challenges. This methodology promotes higher communication and collaboration between development and testing groups. Using this methodology, you can detect defects early in the improvement course of by testing both top-down and bottom-up concurrently. During this part, use stubs to replace lower-level modules, guaranteeing that the top layers can be tested with out waiting for the decrease layers to be fully developed.

This follow ensures adequate coverage of all requirements by the check cases and provides proof of complete coverage. Testers can also determine inconsistencies or gaps and guarantee perfect alignment of the take a look at strategy with project goals. This practice provides priceless inputs for check planning and making a practical test method. You can go so far as involving stakeholders in identifying crucial check scenarios, defining acceptance criteria, and validating test outcomes.
And finally, it must be permitted by the executive authorities for the clearance of the client’s/company’s policies and phrases & conditions. Authorized individuals/team leaders should record and sign off on this course of. Describing the model and highlighting the adjustments chronologically is essentially the most crucial facet of documenting release controls.
- Some checks plans will depend on the storage features of take a look at framework to ensure that take a look at information is saved and retrievable.
- Enterprises want to discover out success according to a quantitative standard.
- Such assessments help identify any constraints or useful resource gaps upfront, making room for proactive redressal measures.
- Each of those actions must be examined, which is called implementation testing.
- I suspect that you simply meant “integration testing”, since that is commonly used, particularly in contrast to unit testing.
Primarily, there are two types of methodical testing approaches- failure-based and experience based. Models additionally serve as the muse to generate check cases by helping testers derive inputs, expected outputs, and test eventualities. In truth, models mechanically create check cases utilizing methods like mannequin transformation, model coverage evaluation, or model-based testing. As a end result, these systematically derived check circumstances provide complete coverage of various system functionalities. A thorough assessment of resource requirements is a should to allow effective planning, useful resource allocation, and take a look at management. A pragmatic and fruitful check strategy can solely result from a transparent understanding of the sources required, such as take a look at instruments, skills, variety of testers, test environments, etc.
For example, in the Development Phase of the SDDP, builders will create and execute unit exams in opposition to supply code. In the General QA part, testers and check engineers will test UI of an application, in addition to service and API endpoints. Once your test plan and scenario strategy are set up, training testers shall be essential to ensure that the goals of checks can be achieved. Testers should be knowledgeable business customers who only want minimal coaching. If you’re executing a User Acceptance Testing (UAT), define eventualities that the tester must execute and confirm that they’re assigned relevant transactions with their management.
Test Managers are additionally answerable for making a schedule for test execution, detailing the order for execution of each automated and guide tests. This detailed explanation will enable other software program testers to conduct the test reliably and persistently irrespective of their expertise. Ensuring that the group is prepared for executing the check design is an important a part of take a look at implementation course of.
Transform Your Business With AI Software Development Solutions https://www.globalcloudteam.com/ — be successful, be the first!
What’s Containerization? Containerization Explained
It additionally happens to be a extensively used host for these looking to deploy Docker images. Containerization is a way to bundle software program code and necessary assets into an unbiased unit that can run on any operating system. Below, you’ll find a way to explore what containerization is, how it started, what benefits you may expertise using containerization, and examples of main industries that use this method. This chain is often a delicate steadiness, and disruptions in one half can have ripple effects all through. Hence, robust freight services, mixed with efficient warehousing, inventory management, and demand forecasting, are pivotal for ensuring that products attain consumers in a timely and cost-effective manner.
Cloud Foundry’s Garden is an open supply possibility that offers containerization as a part of its Platform-as-a-Service choices (PaaS). Cloud Foundry is the host for developing, testing, and deploying portable functions on a cloud server. Because container applications can run on cloud servers, they are typically extra accessible than other functions. A key part of virtualization is isolation, the act of segregating sources for each utility. Container engines carry out higher than digital machines in terms of isolation. But the selection to make use of one over the opposite needs consideration, and depends on the use case.
This functionality allows much more containers to run on the identical compute capability as a single VM. This functionality drives higher server efficiencies and, in flip, reduces server and licensing prices. Kubernetes is a popular open-source container orchestrator that software program builders use to deploy, scale, and manage an unlimited number of microservices. The declarative mannequin ensures that Kubernetes takes the suitable motion to fulfil the requirements based mostly on the configuration recordsdata. Software builders can troubleshoot and change the applying code without interfering with the working system, hardware, or other software services. They can shorten software release cycles and work on updates quickly with the container model.
Isolation
Containerized applications’ isolated functioning mitigates a compromise’s gravity during a security breach. Even if malicious code penetrates the functions, the container vacuum protects the host system from widespread infections. Containerization’s benefits are fairly evident as containers present higher functionality and application assist.

Appropriate gear is needed to manage the complete container load of a container shipping line. The modern design of those mega-ships optimizes house usage, permitting for larger cargo loads. Enhanced storage capacities imply fewer trips for a similar volume of products, lowering fuel consumption and general emissions per container foundation.
Orchestration instruments like Kubernetes, OpenShift, and Rancher, manage how multiple containers are created, deployed, and work together. Docker produces the containerized piece that allows overfitting in ml builders to package deal applications into containers through the command line. These applications can operate in their respective IT environment with out compatibility points.
Each system has advantages and drawbacks, so selecting the best software for the job is essential. Container orchestration is the method of managing and coordinating the usage of containers in a distributed system, including managing the deployment, scaling, and networking of containers. CloudThat is a quantity one supplier of cloud training and consulting providers, empowering individuals and organizations to leverage the complete potential of cloud computing. With a dedication to delivering cutting-edge experience, CloudThat equips professionals with the abilities needed to thrive within the digital period.
Professional Certificates Program In Cloud Computing And Devops – Iitg
Containers ensure that the applying runs the same in each stage of the development cycle, which facilitates continuous integration and continuous deployment. Virtual machines, or digital computing environments that run on top of physical hardware with the help of a bit of software known as a hypervisor, provided that better means. Software working on a digital machine comes packaged with its own guest working system, which makes it much less likely to break due to incompatibilities with the host OS.
In a comparatively short period of time, leaders across industries also had to wrap their minds around containerization explained public cloud choices, DevOps, edge computing, synthetic intelligence and other improvements. In the past 15 years or so, software program growth has targeted intently on enhancing stability, or avoiding broken code and downtime, Hynes mentioned. Test-driven improvement and other agile principles, like YAGNI, helped make software simple, adaptable and secure.
Ignite Your Information In Aws Cloud Operations
- There are many specific container security considerations you have to account for when containerizing applications.
- A key element of virtualization is isolation, the act of segregating assets for every application.
- Enhanced storage capacities imply fewer journeys for a similar volume of products, reducing gas consumption and total emissions per container foundation.
- Boasting years of collective wisdom and a roster of skilled veterans, we offer thoughtful insights, strategic steering, and sensible proficiency in orchestrating container migrations and beyond.
- The completely different microservices talk with each other by way of a shared interface like an API or a REST interface.
Containers share the host system’s kernel but isolate the runtime setting of the appliance, compared to traditional virtualization, the place every virtual machine has its personal working system. Containers permit developers to bundle and run applications in isolated environments, a process often identified as containerization. They share the host system’s kernel and use fewer sources, which implies you’ll be able to run extra containers on a given hardware than VMs. Kubernetes is an open source container orchestration platform that helps handle distributed, containerized purposes at large scale. You inform Kubernetes where you need your software program to run, and the platform takes care of just about everything it takes to deploy and manage your containers.
One solution to this downside is to make use of container-specific networking options. These provide a digital network that containers can use to speak with each other. They additionally permit you to management the community traffic between containers, improving safety. Persistent storage is one other challenge that organizations typically encounter when adopting containerization. Containers are ephemeral, which means they aren’t designed to store information permanently. Containerization is a much less heavy choice to full-machine virtualization, encapsulating an app in a container with its personal setting.
Enhanced with advanced navigation techniques, optimized hull designs, and eco-friendly technologies, these vessels transport vast quantities of products with increased effectivity and lowered environmental influence. The modern container ship can tackle the total container load of several conventional cargo ships. The concept of utilizing containers for transportation dates again to the early twentieth century when railway firms began utilizing picket packing containers to carry and defend fragile items during transit. Malcom McLean’s invention of intermodal transport containers within the mid-1950s revolutionized global trade by permitting easy switch between vans, trains, and ships with out unloading cargo.
Containerization presents a variety of benefits, together with architectural modularity, application responsiveness, fault isolation or failure prevention, and platform independence. That’s one of the main the cause why container utilization is rising globally with a constructive development of over 30% year-over-year. As a platform-agnostic solution, containers are decoupled from any dependencies. Development groups can easily arrange and use containers regardless of the OS or platforms. The largest competitor to Docker, CoreOS’rkt (pronounced CoreOS “rocket”) is a low-level framework that uses methods to create foundational applications.

It doesn’t matter who is handling it, giving the client more energy to select from different providers. Containers are much smaller, typically measured by the megabyte and not packaging anything bigger than an app and its working setting. Explore how IBM’s cutting-edge technologies may help https://www.globalcloudteam.com/ you harness the power of information, streamline operations and gain a competitive edge.
An Introduction To Cucumber Test Automation
Step Definitions in the context of BDD and TDD frameworks are the code that defines the actions for each Explainable AI step in a check state of affairs. They are written in those programming languages used to implement the steps in Gherkin. Some of the most commonly used programming languages for writing step definitions in Cucumber are.
Step 3: Create Step Definition Directory
It’s a proven method of enhancing communication, collaboration, and understanding of software program habits. While acknowledging the pivotal importance of testing, BDD’s core goal is to help everybody collaborate in a method that ensures the software works the method in which it is supposed to. Before learning software testing, you need to https://www.globalcloudteam.com/ have fundamental knowledge software program testing, System behaviour, and hand-on experience of some testing instruments. Yes, Cucumber is often used in Agile environments as it supports collaboration between developers, testers, and stakeholders. It aligns properly with Agile principles by encouraging iterative improvement and clear communication via BDD. Cucumber is a testing software designed for Behavior-Driven Development (BDD), specializing in writing human-readable test eventualities in Gherkin.
Frequent Cucumber Challenges With Resolutions
This tutorial is designed for testing professionals similar to developers, analysts, and testers who are meaning to learn the fundamentals of Cucumber and want to put it into practice. It follows a BDD (Behavior Driven Development) framework to watch the habits of the software’s functionalities. Behavior Driven Development (BDD) is a rising methodology to check and verify your code. It is primarily used to write down and run unit exams for Java applications, supporting a TDD workflow. As you presumably can see, each of the BDD steps above have been linked with its corresponding take a look at definition. You can create a category that would be the entry level for working your Cucumber exams.
Cucumber: What It Is And Best Practices For Test Automation
Cucumber testing is a type of behavior-driven improvement (BDD) testing that focuses on defining and testing the conduct of an software from a user’s perspective. Traditional types of testing, then again, usually give consideration to testing the performance of an application based mostly on its technical specs. Modern teams have a quantity of approaches to software testing at their disposal, every geared toward totally different goals. For example, Data-Driven Testing optimizes the QA process by running the identical exams with numerous enter information sets. There is little doubt that API testing is a critical a part of the software growth course of. By choosing Cucumber, you’ll be able to ship high-quality APIs and ensure that different app components perform appropriately.
- Just like Cucumber’s main focus, BDD locations a central emphasis on communication and efficient collaboration between builders and non-technical stakeholders, such as product managers and clients.
- At the same time, it permits efficient verification and residing documentation of the system’s behavior.
- Whether you’re testing web purposes, APIs, or backend providers, Cucumber is a useful device for creating meaningful checks that align with business targets.
- Let’s take an overview of the method to make the most of the Cucumber testing framework.
- DEV Community — A constructive and inclusive social network for software program builders.
It includes crafting totally different take a look at instances in the type of easy-to-understand English statements inside a manually-generated feature file. These statements middle across the system’s habits and are extremely user-centric. World’s first end to end software program testing agent built on modern LLM to assist you plan, creator and evolve tests utilizing natural language.
After writing scenarios in Gherkin and corresponding to a step definition, here is how Cucumber testing works. Gherkin provides a shared set of keywords in English that is easily understandable by members from varied backgrounds, thus guaranteeing constant outcomes from take a look at scripts. Even though Cucumber is amongst the most generally used BDD & acceptance testing instruments, it does include limitations that testers and developers should be conscious of.
Cucumber is a device in BDD that focuses on defining a software utility’s behavior with clear examples earlier than coding. It helps foster understanding in builders about the desired conduct of the applying and facilitates seamless collaboration with stakeholders. Cucumber is also helpful in automated testing because it offers clear and simply comprehensible testing scripts for automation and system acceptance testing. Together, they help construct a standard understanding of the software program beneath growth, making certain that it meets the expectations of end customers and enterprise stakeholders. The device was initially developed by Aslak Hellesøy in 2008 to support BDD in Ruby. It shortly gained reputation because of its progressive strategy to software testing.
Cucumber tool was initially written in the “Ruby” programming language. It was exclusively used only for testing of Ruby as a complement to the RSpec BDD framework. BDD consists of test case improvement in the type of easy English statements inside a feature file, which is human-generated. Test case statements are based mostly on the system’s behavior and more user-focused. Cucumber is a Behavior Driven Development device used to develop test cases for the habits of software’s functionality.
However, teams ought to perceive the appliance programming interface specifications earlier than writing checks. They must overview the API’s objective, functionality, endpoints, request methods, expected request codecs, and response structures on the very start. Cucumber is a BDD framework that permits writing check instances in Gherkin syntax—a human-readable language that makes use of keywords corresponding to Given, When, and Then.
This lets you combine the ability of Cucumber’s collaboration options with specialised testing capabilities. Teams that adopt Cucumber testing can proactively resolve points within the early levels of the event cycle, resulting in the well timed supply of high-quality software program. With its emphasis on readability, maintainability, and reusability, Cucumber testing remains a tool for modern software program development. It empowers teams to create user-centric applications that meet evolving market demands.
These are written in a programming language (e.g., Java, Ruby, Python) and embody logic that interacts with the appliance underneath take a look at. Cucumber uses annotations (such as @Given, @When, @Then in Java) to bind Gherkin steps to specific strategies within the code. When Cucumber parses a step like “Given the person is on the login web page,” it looks for a method annotated with @Given that matches the text. This plain language method allows non-technical group members to take part actively within the testing course of, making certain that the software program behaves as expected from a user’s perspective. Another highlight is that specs written in Cucumber serve not solely as guides but also as executable automated tests. This means that documentation isn’t static; it evolves and validates constantly because the project progresses.
Cucumber exams are linked to step definitions written in a programming language, that are then executed to verify the app’s behavior. Cucumber is an open-source testing device that helps Behavior-Driven Development (BDD), enabling teams to put in writing exams in plain language that anybody can understand. By bridging the hole between builders, testers, and non-technical stakeholders, Cucumber ensures that the software program meets each useful and business necessities.
Behavior-Driven Development (BDD) is a technique in software program growth aimed toward enhancing Test-Driven Development (TDD) practices by integrating agile specification methods. Through these features, the device will ensure that the developed software program is aligned with the wants and expectations of the tip person, selling greater quality and customer satisfaction. It integrates necessities specification, documentation, and testing processes right into a single cohesive method.
By employing Cucumber, you can be positive that your exams are easily readable, maintainable, and understandable by all stakeholders involved in the software growth course of. Behavior Driven Development (BDD) is an strategy to software program development that emphasizes collaboration between builders, testers, and enterprise stakeholders. This format not only clarifies what the characteristic ought to do but also creates a directly executable check that verifies if the appliance behaves as expected. This simplifies communication amongst team members and ensures that everyone, from builders to stakeholders, clearly understands the aim and operation of the brand new characteristic.
It employs keywords like And, When, Given, Then, and But to articulate the various steps of a take a look at situation. Most corporations are adopting a proactive strategy to harness the facility of software program testing. They’re integrating many essential acceptance take a look at scenarios in development, also called Behavior-Driven Development (BDD).
Top 30+ E-commerce Developers For Rent 2023
Thank you for all your hard work up to now, and I am excited to see what we are in a position to achieve collectively in the future. Start creating extremely safe and scalable ecommerce options to spice up your visitors and skyrocket your revenues. To check the depth of information, you’ll find a way to check how nicely updated he/she stays with the most recent trends. You can also try vetting the applicant’s familiarity with applied sciences deployed in ongoing projects. He has in-depth information of cloud architecture development, software program programming, and front-end & back-end administration. He is extremely expert in applied sciences such as React, Bootstrap, CSS, Firebase, GitHub, MySQL, etc.
But hiring for a technical profile is normally a advanced task, especially with out prior expertise. This information has been curated with the only purpose of serving to to rent one of the best expertise on your organization. At our company, we offer dedicated eCommerce net designers who focus on creating visually gorgeous and user-friendly online stores. Our group of builders has years of experience working with eCommerce platforms such as Magento, Shopify, WooCommerce, and more. Our designers can create a customized design that reflects your brand’s identification and helps your on-line store stand out from the competitors. Whether you’re trying to build a new on-line store from scratch or redesign an present one, our group may help you every step of the greatest way.
Our cost-effective and versatile engagement models put your group in a position to derive the maximum value from our eCommerce website developers’ capabilities. This reduces the trouble for the purchasers, and our devoted E-commerce builders work over a full-time or an hourly foundation primarily based upon your necessities. The shoppers are hence ready to ensure that short-term initiatives are effectively completed at reasonably priced prices.
Hire Ecommerce Builders On-line – Discover Freelancers
Choosing Fireart as a tech associate, you rent dedicated Magento developers who can convey your business to the following degree. An e-commerce developer creates a web site, so naturally, they must be adept within the basics of internet growth. Be certain to search out someone who knows tips on how to code and build front-end and back-end techniques.
Daily standups are mandatory for each Turing developer as they maintain the developer and the customer in alignment with the mentioned objective. All Turing distant e-commerce developers work for at least four hours in your time zone in your comfort. But in the long run, experience is the most important thing in an eCommerce developer. At ProCoders we value diverse tech information and continually improve upon our abilities. We’ve already worked with start-ups and small enterprises in numerous industries, so that you might wish to check out our prior initiatives.
Not even mentioning obligatory prior experience with Shopify, BigCommerce, Magento, Volusion, Woocommerce, and other eCommerce platforms or tools on your E-store. You can also want to know the average hourly price for app developer. Web improvement becomes increasingly more specialised because of the intricacy of programming applied sciences, each with its own set of programming languages, integrating instruments, and growth approaches. Hiring certified eCommerce internet developers is a should when you should develop a website that really generates site visitors. With a useful and optimized platform, you’ll have the ability to entice customers and build brand loyalty.
Working with numerous enterprise fashions, he’s supplied options that fit necessities and budgets. Donald has experience collaborating as a valuable group member for enterprises and being a self-managed only-developer for startups. While working with Donald, shoppers can count on much less back and forth, to-the-point solutions for requirements, straightforwardness with task feasibility, and a solution provider and executor. When tasked to rent E-commerce builders it is very important vet the extent of knowledge of the candidates. Here’s an inventory of questions that you simply use to check the information of builders. For this, vetting past experiences of developers working on UX turns into important.
Our Ecommerce Web Development Services
We provide SafePay fee safety and your selection of most well-liked cost methodology for monetary peace of thoughts. The billing is done on a periodic foundation similar to 2-4 weeks (Monthly) for giant and longer-term initiatives. The billing is finished in accordance with a set project value for bigger initiatives with definitive requirements.
- Our E-commerce improvement providers are conducted in accordance with the most effective industry practices and strengthen your small business.
- Partnering with companies like ProCoders, which offers employees augmentation and outsourcing services, greatly facilitates the process of creating an eCommerce platform.
- It is just about inconceivable to place together a staff of “full-stack” programmers, that’s why plenty of firms choose to rent an eCommerce developer specifically for their projects.
- It’s a devoted expert professional who has specialized information of the instruments and platforms that are typically utilized in eCommerce businesses.
We verify if the candidate really needs to work at your company and is prepared to spend 5+ hours to show it by rigorous tests. We wanted some short-term work in Scala, and Toptal discovered us an excellent developer inside 24 hours. This merely would not have been potential via another platform.
Top 10 E-commerce Developer Interview Questions
Fireart Studio offers a complete suite of companies, together with Mobile App Development, Web Development, Product Redesign, UI/UX & Branding, Animation, and Digital Illustration. Since 2013, more than seven hundred forward-thinking firms have entrusted us with a full design and improvement course of. With Turing, you possibly can rent one of the best distant builders for 100+ abilities such as React, Node, Python, Angular, Swift, React Native, Android, Java, Rails, Golang, PHP, Vue, DevOps, Machine Learning, etc. Turing also provides builders based on tech stack and seniority. Knowledge of web site testing is another fundamental task that E-commerce developers should undertake.
Access a vast pool of skilled developers in our expertise network and hire the highest 3% within just forty eight hours. Toptal provides a no-compromise resolution to companies present process fast growth and scale. Every engineer we have contracted via Toptal has quickly integrated into our team and held their work to the very best standard of high quality while sustaining blazing development velocity.
See what niches do the developer mention when mentioning methods of staying up to date. We will assist you select the best skills and spot a SKILL developer who will slot in your company culturally. We hired about 16 ML engineers from Turing which lowered our hiring effort by 90% as in comparability with other distributors. Turing has been providing us with high software program builders in Latin America.
Open communication channel for streamlined interactions, brainstorming periods, and doubt resolution. Once satisfied with the interview, the useful resource might be hired. Tell us the talents you need and we’ll find one of the best developer for you in days, not weeks. Neil Roseman shares insights on how to conduct in-depth technical interviews. Check whether or not the developer is ready to answer the mentioning the flexibility to update sections of an internet web page.
Of Toptal Purchasers Select To Rent Our Expertise After A Risk-free Trial
We make the most effective of Weebly’s prime eCommerce features based mostly on your business necessities. You can hire Weebly developer from us for a winning Weebly web site http://rpk-fusion.ru/otdelka-sten-panelyami/. We specialize in all features of Wix eCommerce development, corresponding to EditorX, which simplifies making responsive on-line malls.
This will also help to avoid the state of affairs when you hire an eCommerce developer who focuses on Shopify to develop a net site in WordPress. Partnering with firms like ProCoders, which offers workers augmentation and outsourcing providers, tremendously facilitates the method of creating an eCommerce platform. Even if you already have a working website but wish to add new features, redesign, or wrap up a code, if you want to transfer it to another platform – these are the first clues that you just need an eCommerce developer. Relying only on your own strength is irrational when you can turn to a professional. In the tip, appearing blindly can damage your project and you’ll be back to square one.
He has delivered initiatives in CI/CD, Devops, Software engineering, agile project management, Testing TDD/BDD, IT technique, and IT course of. James is a full-stack internet and mobile app developer with 9+ years of experience in designing and growing person interfaces, testing, debugging, and deploying websites and cellular applications. Toptal makes discovering a candidate extremely simple and gives you peace-of-mind that they have the abilities to deliver. I would positively recommend their providers to anyone looking for highly-skilled developers.
They primarily cope with three important vitamins that vegans want, i.e., B12, Vitamin D3, and DHA/EPA Omega 3. Choose from a quantity of payment methods with SafePay payment protection. Compare the Quotes you receive and rent one of the best freelance professionals for the job. Create your free job posting and start receiving Quotes within hours. Our devoted help group works 24/7 to resolve all of your queries over the telephone or e mail, regardless of where you are positioned.
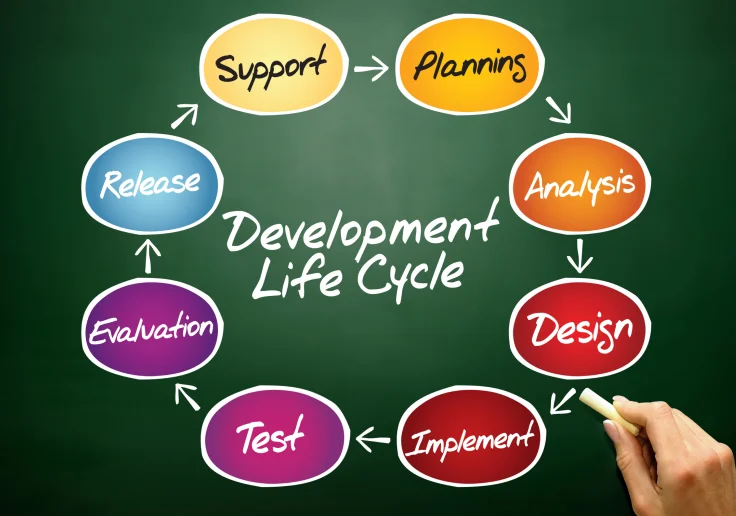
What Is SDLC? Understand the Software Development Life Cycle
Try out Stackify’s Retrace tool for free and experience how it can help your organization at producing higher-quality software. Each phase has its own mini-plan and each phase “waterfalls” into the next. The biggest drawback of this model is that small details left incomplete can hold up the entire process.
- Other SDLC models include rapid application development (RAD), joint application development (JAD), the fountain model, the spiral model, build and fix, and synchronize-and-stabilize.
- SDLC strategies have been around since the 1960s, and most of its core concepts have evolved over time.
- It lacks the thorough requirements definition stage of the other methods.
- This process goes on until customers have no more negative feedback, after which the team gets a customer-driven requirements analysis and starts developing the final product.
- This is a feasibility study or preliminary plan for the company to acquire any resources necessary to improve a service or build on specific infrastructure.
- This high-level description is then broken down into the components and modules which can be analyzed, designed, and constructed separately and integrated to accomplish the business goal.
In systems design, functions and operations are described in detail, including screen layouts, business rules, process diagrams, and other documentation. Modular design reduces complexity and allows the outputs to describe the system as a collection of subsystems. This may involve http://www.norge.ru/news/2011/03/07/14136.html?page=window&t= training users, deploying hardware, and loading information from the prior system. SDLC can be used to develop or engineer software, systems, and even information systems. It can also be used to develop hardware or a combination of both software and hardware at the same time.
Core Problems with Software Risk Management
During the testing stage, developers will go over their software with a fine-tooth comb, noting any bugs or defects that need to be tracked, fixed, and later retested. The analysis stage includes gathering all the specific details required for a new system as well as determining the first ideas for prototypes. First, you have to assess risks and build a risk breakdown structure, which facilitates better and more enhanced analysis. The Agile SDLC model separates the product into cycles and delivers a working product very quickly. Testing of each release feeds back info that’s incorporated into the next version. According to Robert Half, the drawback of this model is that the heavy emphasis on customer interaction can lead the project in the wrong direction in some cases.
Developers are now responsible for more and more steps of the entire development process. Some projects require the team to write user manuals or create instructional videos before the software becomes available to end users. Let’s take a close look at every typical phase of an average software development life cycle. SDLC strategies have been around since the 1960s, and most of its core concepts have evolved over time. The exact number and nature of steps depend on the business and its product goals. On average, most companies define SDLCs with five to seven phases, although more complex projects reach ten or more stages.
Design Plan
Also, make sure you have proper guidelines in place about the code style and practices. The agile methodology relies on ongoing release cycles that make small, incremental changes to the previous release. Builds evolve as teams add new features and improvements with each deployment. The higher management either signs off on the project or asks the team to go back a step in the SDLC and come up with a new suggestion. If you are considering a transition to DevOps, ensure the team has a firm grasp of SDLC strategies before you introduce radical workflow changes. The system analyst is a person who is thoroughly aware of the system and guides the system development project by giving proper directions.
Incident Investigation Methods: Root Trigger Evaluation
An outage is an example of a problem where that is notably essential. The Ishikawa diagram is a a lot most well-liked technique of project managers to carry out a Root Cause Analysis. One might be that the basis cause identified was not the true root trigger, but instead was a symptom. That stated, there are often issues in the actual world where two or three causes all significantly influence a non-conformance. The 80/20 rule applies here, where if a small group of causes make up 80% of the cases of non-conformance, they should all be considered for enchancment efforts. It’s important through the investigation of an issue to achieve all the way all the method down to the foundation trigger and never cease the investigation with one of the symptoms.
It is amongst the seven basic high quality tools figuring out many possible causes for an impact or problem. Effective brainstorming can use a Fishbone diagram to attain stellar outcomes. Start this step by reconstructing a timeline of events in a way that you’ll be succesful of pinpoint exactly what led to the issue and different issues that coexist with the one you’re dealing with.
For example, you discover that extra visits to the gasoline station have been required for a automobile, even though travel utilization has not changed. Upon investigation, you notice that the miles per gallon metric has changed from 25 mpg to 17 mpg. The change in efficiency is a symptom, and never the reason for the issue. With more investigation, you discover that the tire strain isn’t set to specs and is simply too low. This is the root trigger, as the incorrect tire stress is resulting in the change in fuel efficiency. Also known as a causal issue analysis, a causal issue tree analysis permits an organization to document and visually display—using a causal factor tree—every choice, event or motion that led to a particular problem.
- If you’re a leader who needs to problem-solve effectively, here’s an summary of root cause analysis and why it’s important in organizational management.
- It requires the best strategies and instruments, as nicely as leadership that understands what the effort entails and fully supports it.
- It’s a systematic approach that goes beyond just figuring out signs and aims to uncover the foundation explanation for the issue.
- Instead of wanting at the particular day or hour that one thing went mistaken, we look at an extended time period and acquire a historical context.
- Hence, figuring out the foundation causes of an issue helps in developing more practical methods to beat it.
Root Cause Analysis (rca): Definition, Course Of And Tools
Elevate your process improvement game in 2024 with Six Sigma methodologies. Achieve quality excellence with expert insights in this informative blog. Additionally, incorporating lean six sigma green belt training https://www.globalcloudteam.com/ and RCA can additional enhance your ability to enhance enterprise processes and successfully implement Root Cause Analysis. RCA relies on the principle that issues can greatest be solved by correcting their root causes versus different methods that target addressing the symptoms of problems or treating the signs. Root Cause Analysis (RCA) is a method of drawback solving that aims at figuring out the basis causes of issues or incidents. There are many various tools obtainable for determining the root trigger, so remember to choose the right tool(s) in your situation.

Based on your solutions, decide what habits changes are plausible on your root cause evaluation. Research exhibits diverse ideas improve high-level decision-making, which is why you must connect with colleagues with totally different opinions and experience to boost your root trigger analysis’s consequence. According to research described in the Harvard Business Review, eighty five percent of executives imagine their organizations are bad at diagnosing issues, and 87 percent suppose that flaw carries significant prices.
Fixing this downside ought to prevent the whole sequence of occasions from recurring. The real root trigger might be a design concern if there isn’t any filter to forestall the steel scrap moving into the system. Or if it has a filter that was blocked as a result of a lack of routine inspection, then the true root cause is a upkeep issue. Without those insights, you can’t reap root trigger evaluation’s advantages because external forces—including trade trends, opponents, and the economy—can have an effect on your company’s long-term success. Investigators require whatever knowledge is critical to make sure they have the evidence they should perceive the complete extent of the incident and the time frame in which it occurred. After analyzing each potential root trigger, the RCA team determines that the most likely cause was the recent launch of an analogous app by a top competitor.
The Underlying Causes
Automate software program supply for any utility on premises, cloud, or mainframe. When folks make errors or fail to complete required duties (for instance, an employee fails to perform regular upkeep on a bit of apparatus, inflicting it to interrupt down). When real-world materials or equipment fails in some way (for example, a desktop pc stops working or a part from a third-party vendor delivers substandard performance). Third, there could additionally be more than one root cause for a given drawback, and this multiplicity can make the causal graph very difficult to determine.
This is why root cause analysis is commonly thought-about to be an iterative course of. Too many companies use generic buckets like human error and process not adopted to categorise an entire incident. These are low-resolution investigations that lead to weak options. Cause Mapping root trigger ai it ops solution evaluation flattens downside solving by deferring to the individuals within the group who understand how nicely present processes truly work. A robust prevention culture makes it easier for folks to share what they know.
It helps you understand shifting situations round your organization and ensure that your efforts are relevant and sustainable. If you’re a pacesetter who needs to problem-solve effectively, here’s an overview of root trigger analysis and why it’s important in organizational leadership. After amassing the data and mapping occasions, investigators ought to start figuring out the basis causes underlying the incident and working towards a solution. There are several approaches to root cause evaluation, every with its unique methodology and instruments.
There are many different tools, processes and philosophies which have been developed based mostly on Root Cause Analysis. You need to accurately determine the basis reason for an inefficiency in order to derive an answer that will reduce or remove a non-conformance. Be certain to take your time, because when the basis cause is incorrectly recognized, the group is unlikely to find an optimized answer, which finally ends up in wasted effort and time. The root reason for high quality points can often be hidden or impacted by more than one significant factor.
Our RCA software program mobilizes your group to complete standardized RCA’s whereas giving you the enterprise-wide knowledge you have to enhance asset performance and maintain your group safe. The time period ‘RCA’ (Root Cause Analysis) is type of imprecise, deceptive and simply misinterpreted by those that usually are not immersed in its use. It is a useless and counter-productive time period as a end result of there is no universally accepted, standard RCA definition. Therefore, any process/tool somebody is utilizing to unravel a problem is likely to be labelled as ‘RCA’. Once the agreed actions are carried out, the staff closes the process by validating utilizing a speculation and convicting them or setting them free. Discover the means to create a powerful compliance culture in your organization.
Since every Causal Factor can have multiple root causes and because most incidents have a quantity of Causal Factors, most incidents have a number of root causes. There is not any definition of root cause “THE Root Cause.” There are a number of root causes for a single incident. In the TapRooT® Root Cause Analysis System, we use the Root Cause Tree® Diagram and Dictionary to seek out the root causes of Causal Factors.
It’s designed to equip leaders and groups with the instruments to do their best work–to the safest and highest commonplace. All you should do is start with an issue statement after which ask “Why? While there are many totally different approaches to Root Cause Analyses, a lot of the methods boil down to the following five steps. In the Japanese evaluation methodology 5 whys the query ‘why’ is asked five times.
12 Real-World Examples Of Natural Language Processing NLP
For example, capitalizing the first words of sentences helps us quickly see where sentences begin. The simplest normalization you could imagine would be the handling of letter case. Computers seem advanced because they can do a lot of actions in a short period of time. Understand the overall opinion, feeling, or attitude sentiment expressed in a block of text.
If they are loaded with CTAs, the search intent is transactional, and if there are many web pages of the same website, chances are the search intent behind the keyword is navigational. The SERP analyzer helps you get instant content ideas based on the most successful content for a keyword. But with a little bit of natural language, you can be sure that your content ranks higher on search engines. It might even get picked to be a featured snippet, or a website in the ‘People also ask’ section.
Natural Language API
There are other non-SEO tools that can help you optimize your site for natural language search. For example, business-to-business SEOs looking to optimize for their buyer personas’ natural language search questions might try CallRail or Chorus.ai. Both solutions offer Conversation Intelligence, which highlights essential phrases in call transcripts. If multiple customers ask the same questions on calls, other potential customers will likely ask the same, and you can leverage these as natural language search terms. Now that you have a fuller idea of your personas and their intent, you need to create great content for them. In terms of natural language search, try to anticipate the questions your users are likely to ask.

Tools like keyword extractors, sentiment analysis, and intent classifiers, to name a few, are particularly useful. Using NLP, more specifically sentiment analysis tools like MonkeyLearn, to keep an eye on how customers are feeling. You can then be notified of any issues they are facing and deal with them as quickly they crop up. Similarly, support ticket routing, or making sure the right query gets to the right team, can also be automated. This is done by using NLP to understand what the customer needs based on the language they are using.
Which Natural Language product is right for you?
But keyword searches are not an intuitive way for users to ask questions, and users are actually pretty bad at using them to find what they need. They force users to strip out question words and natural language search engine examples other connective language to form literal text strings that the search engine can use to query data. It also may require effort on the part of the business to mine intent from keyword searches.

Featured snippets are a fundamental part of the SEO pro’s arsenal. Google voice search devices often recite featured snippet content when responding to search requests. Thus, BERT and natural language search mean more valuable snippets for SEO professionals to aim for. All these changes help search engines better adapt to changes in search behavior. These new advances in search will help answer more complex search questions.
Join our vibrant Facebook community and dominate SERP with AI-powered SEO & content marketing
They need the information to be structured in specific ways to build upon it. Train custom machine learning models with minimum effort and machine learning expertise. Natural Language with Speech-to-Text API extracts insights from audio. Vision API adds optical character recognition (OCR) for scanned docs.
The goal of every search engine is to supply its users with the most accurate and relatable results it can, and natural language search is the next step in that mission. Far exceeding the days of Archie and the endless cramming of meta keywords into HTML or Javascript codes, natural language search allows users to ask questions comfortably and expect strong answers. Natural language search engines are made to understand conversational language so that users can express themselves naturally and get the most relevant information from their search queries.
NLP in Google search is here to stay
I also made an unexpected discovery when researching this article, which is that Ask Jeeves is not the only natural language question and answer service left over from the 90s. START is a “natural language question answering system” developed by the InfoLab Group at MIT, and it has been online since 1993. This is as opposed to keyword-based search, which is what most people who are used to using web search engines still default to. Keyword-based search is an attempt to break down a query into the most important terms, getting rid of unnecessary connecting words like “how”, “and”, “the”, and so on.
- For an ecommerce use case, natural language search engines have been shown to radically improve search results and help businesses drive the KPIs that matter, especially thanks to autocorrect and synonym detection.
- The simplest way to handle these typos, misspellings, and variations, is to avoid trying to correct them at all.
- Instead, they help Google rank web pages based on the meaning of the entire text.
- NLP continues to evolve, to empower the query-level functionality of keyword search – which will remain as the go-to method to handle the simple queries that we perform on a daily basis.
- RankBrain was introduced to interpret search queries and terms via vector space analysis that had not previously been used in this way.
Gain real-time analysis of insights stored in unstructured medical text. Microsoft has explored the possibilities of machine translation with Microsoft Translator, which translates written and spoken sentences across various formats. Not only does this feature process text and vocal conversations, but it also translates interactions happening on digital platforms.
Use long tail keywords in your content
As with any other kind of keyword search, you just need to type your natural language search terms into your search bar. You can also use a voice assistant (think Google Home or Siri) to conduct a natural language search. But we’ll get to them, and how they’re changing the SEO landscape, shortly. In this article, we’ll dive deep into natural language processing and how Google uses it to interpret search queries and content, entity mining, and more.
These long-tail keywords have lower traffic, but they also come with less competition and more conversion potential. Long-tail keywords lead to 4.15% more conversions than their shorter cousins. Natural language search will naturally produce more long-tail keywords. And more long-tail keywords mean more potential conversion value for SEO professionals. BERT plays a role not only in query interpretation but also in ranking and compiling featured snippets, as well as interpreting text questionnaires in documents.
How Natural Language Search Engines Work
They would also use other search parameters, but the search system was inherently flawed for several reasons. First, users would naturally want to type in actual questions, but the search engine would get bogged down looking for results that include the extra words. Now, it might seem like a big process to integrate a natural language search engine into your website.
And search engines have worked hard to meet this expectation, so that people will feel satisfied with the service they provide instead of frustrated by it. Natural language search is search carried out in everyday language, phrasing questions as you would ask them if you were talking to someone. These queries can be typed into a search engine, spoken aloud with voice search, or posed as a question to a digital assistant like Siri or Cortana.
Nearly two decades later, Google and other search engines started to realize the value of natural language search and further develop the experience that Ask Jeeves was trying to provide. Join us as we go into detail about natural language search engines in ecommerce, including how and why to leverage natural language search and examples of ecommerce use cases in the wild. There’s a possibility that we’ll see natural language search developing in a few different directions as Bing furthers its ‘conversational’ search style, and other search engines play to their own strengths. Natural language search is bound up with all of these, since these are all capabilities that would allow Google to better interpret and respond to search queries in everyday language. So I think it’s fair to say that we can expect much better and more accurate natural language responses from Google as these algorithms learn, develop and have their limits tested. There’s a reduced patience for sitting and trying different keyword combinations; people are searching on their mobiles, on the go, and they want to be able to ask a question, get the answer, and move on.
SaaS vs IaaS vs. PaaS: Differences, Pros, Cons and Examples
For companies that are looking to implement a specific function or a singular business process, SaaS is a good choice. The lines have blurred between IaaS and PaaS, as the major cloud providers offer both from the same environment. IaaS can help organizations find efficiencies with hardware and facilities costs, but PaaS can further reduce administrative overhead and expand usage to less technical customers. Yes, many businesses use a hybrid approach, combining different cloud service models to meet their specific needs. For example, a company might use IaaS for its infrastructure, PaaS for application development, and SaaS for specific software applications. SaaS is a cloud computing service model that delivers software applications over the Internet.
The diagram “As-a-Service” below illustrates the differences between IaaS vs PaaS vs SaaS and the level of vendor management that you get with each service model. Learn all about IaaS vs PaaS vs SaaS and how they help create a cloud-computing environment that is tailored to your needs. We’ll also take a look at some examples, so you know how as-a-service options integrate into your current IT landscape and what benefits and disadvantages to expect.
Difference Between IAAS, PAAS, and SAAS
IaaS helps the user save time and costs as the service provider manages the hardware setup. Since the resources are used only when needed, it abolishes the wastage of unused resources, and one has to only pay for the resources paas saas iaas difference they use. Infrastructure as a Service provides the fundamental building blocks for cloud infrastructure, as well as computing resources like processing power, virtual machines, networking, and more to its users.

IT departments would rather turn management over to someone else and focus more of their limited IT resources on things that are going to help the agency. IaaS and PaaS are both all excellent resources for moving your physical hardware, workflows, and tools to a cloud environment. Instead, each offers some unique benefits of cloud computing that the other doesn’t. However, like IaaS and other cloud services, virtualization still has its limitations. The virtualized components available through the internet are equivalent to the servers and hardware companies would traditionally store in their building. With a Software-as-a-Service product, you are getting the most service from your third-party provider in terms of software management and maintenance.
IaaS vs PaaS vs SaaS: Explaining the Key Differences
If you’re a startup or a business giant and require a “pay-as-you-go” cloud computing model, IaaS is the right choice. It is especially a savior for growing and established businesses because it gives them the freedom to scale anytime. How simple do you want it to be to build and manage the environment that hosts your DevOps delivery pipeline and applications? One term you’re likely seeing more frequently in the world is XaaS, short for Everything as a Service. Anytime you are unsure of a new application’s demands, IaaS offers plenty of flexibility and scalability. PaaS may not be a plug-and-play solution for existing legacy apps and services.
What cloud computing allows for is the allocation of one, several, or all of the parts of your infrastructure to the management of a third party, freeing you up to focus on other things. “As-a-service” generally means a cloud computing service that is provided by a third party so that you can focus on what’s more important to you, like your code and relationships with your customers. Each type of cloud computing leaves you less and less on-premise infrastructure to manage. Choose a SaaS CRM solution, offloading all day-to-day management to the third-party vendor, but also giving up all control over features and functionality, data storage, user access and security. Typically IaaS customers can choose betweenvirtual machines hosted on shared physical hardware or bare metal servers on dedicated physical hardware. Customers can provision, configure and operate the servers and infrastructure resources via a graphical dashboard, or programmatically throughapplication programming interfaces .
Discover AWS Solutions
From e-commerce to short-term projects, SaaS is the quickest and easiest solution if you don’t need highly customized applications. SaaS is also a great option for applications that are not used very often, e.g. tax software. You can even include other vendors and stay flexible during the entire process. PaaS is also the way to go if your organization requires customized applications that need to be developed and deployed in a short amount of time. As cloud computing continues to transform the way businesses operate, organizations are increasingly looking to… All three models offer scalability, but IaaS provides the most control over resource allocation, while PaaS and SaaS handle scaling automatically based on user demand.

In general, PaaS costs more than IaaS because with PaaS, you pay for DevOps tools, the infrastructure that hosts those tools and any applications you run on the infrastructure. PaaS platforms tend to offer a variety of integrations that make it easy to connect your DevOps pipeline to external tools or resources that address needs such as security and access control. Additional resources and training may be required for the workforce to learn how to effectively manage the infrastructure. Customers will be responsible for data security, backup, and business continuity. Due to inadequate control into the infrastructure however, monitoring and management of the resources may be difficult without adequate training and resources available inhouse.
Cloud Computing Deployment Models
Full access is granted through virtualization technology via dashboard or API. This way, clients have complete control over their computing infrastructure. Cloud computing service models provide organizations with cost-effective, scalable, and flexible solutions that can be tailored to their specific needs. SaaS products are among the most popular cloud computing services used by companies to build and grow businesses. SaaS is highly scalable and easy to use and manage because it doesn’t always require download and installation on individual devices for entire company use. This is particularly helpful for global teams that don’t work in close proximity.

Startup Program Get financial, business, and technical support to take your startup to the next level. Startups and SMB Accelerate startup and SMB growth with tailored solutions and programs. Marketing Analytics Solutions for collecting, analyzing, and activating customer data.
IaaS vs PaaS vs SaaS: Three Options — One Solution or How to Choose Between the Alternatives [2023 Update]
Migrate to Containers Tool to move workloads and existing applications to GKE. Medical Imaging Suite Accelerate development of AI for medical imaging by making imaging data accessible, interoperable, and useful. Cloud SQL Fully managed database for MySQL, PostgreSQL, and SQL Server. AlloyDB for PostgreSQL Fully managed, PostgreSQL-compatible database for demanding enterprise workloads. Google Cloud Deploy Fully managed continuous delivery to Google Kubernetes Engine and Cloud Run. VMware Engine Fully managed, native VMware Cloud Foundation software stack.
- It also uses the pay-as-you-go model, so you don’t have to pay extra bucks.
- It makes sense for companies to use SaaS products that meet their business requirements because they can quickly be more productive.
- New resources can be provisioned whenever they’re needed, enabling rapid scaling in response to new business needs.
- Each model offers an alternative to managing your own on-premises data center, but the service provider will manage different elements in the computing stack depending on which type you choose.
- ‘Network fabric’ is a general term used to describe underlying data network infrastructure as a whole.
It totally depends upon the customer to choose its resources wisely and as per need. In case you use obsolete applications, it may turn out that they do not function properly with PaaS products. Therefore you will need to improve your application and proceed with investments in configuration changes for its flawless functioning. Some changes in the architecture made by vendors may cause serious problems. For example, you use a particular framework compatible with the cloud solution, but a provider releases an update, which requires another framework for further compatibility. As a result, you will have to change a PaaS provider or switch to another framework.
L’IaaS, le PaaS et le SaaS avec Red Hat
By distributing the same service through multiple interfaces, IaaS providers ensure that all users will have complete access to their computing infrastructure. These entire cloud application services are the most common form of cloud computing. They are ready-to-use and often https://www.globalcloudteam.com/ run directly through the client’s web browser, meaning there is no need for installations or downloads like it with on-prem solutions. For example, if I wanted to create an app for my business, I would use a PaaS product, and it would act as the platform for my app to run on.
